M2M Device Networking:
Enabling New Possibilities for Preventive Maintenance (cont.)
By Marty Huff

(Go to page 1 of Device Networking Technology Article)
The Gateway: Translates and Passes The Data To The Network
The gateway is responsible for extracting raw data from the intelligent device and preparing it for the network. Gateways are typically hardware but can also be a combination of hardware and software.
Gateways use a protocol such as Modbus or a proprietary device driver to interact with the intelligent device, and translate the data into a format that another device, software application or human can understand. The gateway can also act as, or interact with, a Web server to serve files to Web browsers, allowing multiple simultaneous connections to Web pages. Gateways may also have other enhanced functionality such as the ability to convert media types (e.g., serial to Ethernet). For example, a gateway such as Advantech's WebLink can communicate with intelligent devices via serial, Ethernet, and/or USB connections. With a PCMCIA cellular modem acting as the network connection, the WebLink can also collect and send data via cellular service.
For M2M networks. Cellular data transfer overcomes most limitations of distance and location.
the network: the connectivity that serves data to the remote client
In an m2m application, the network is like any other network: it is the connection that allows data to pass from one place to another. The four most popular network connectivity choices in an M2M system are:
- Wired Ethernet
- Wireless (802.11x, Bluetooth, 802.15...)
cellular - Pots (plain old telephone service)
Wired Ethernet is often used when the intelligent device is part of an existing LAN or can be connected to an existing LAN. The device can then be accessed by another device, software application, or human at the same location, or via the internet using the existing internet connection on the LAN. Wired Ethernet is completely secure as long as any internet connections on the LAN are carefully protected by a firewall. A local area network also has, by far, the highest data transfer rates.
|
Wireless is a good choice when wires are not feasible and devices are within short range of each other. Wireless technology is cost-effective, secure, and stable, but very limited by distance. With a wireless network, you can create an always-on connection between the intelligent device and an existing LAN or other wireless-enabled device, with the data transfer rate much higher than a cellular or wired modem. Security is more of an issue than with wired connections. Rather than a standard firewall, wireless devices require different security measures, for example, encryption or IPSEC. Currently, the two most popular wireless technologies are Wi-Fi (802.11x) and Bluetooth. Zigbee (802.15) is a new wireless protocol designed specifically for direct machine-to-machine communications.

Cellular data modules and cards are becoming increasingly popular third party applications or custom software programs are used to facilitate machine-to-machine communications, provide an operator interface, and provide web browser access and internet presence. One such program is Advantech Studio (A-Studio) provides all of the necessary tools to communicate with the device, web-enable the application, and deliver data securely to all levels of the enterprise. A-studio provides a user friendly "drag and drop" programming environment. Microsoft's .Net platform also provides the tools necessary to program a custom m2m application for both embedded and non-embedded platforms.
Cellular tends to be more expensive than other connection types and is not the best choice for applications that require high bandwidth and real-time, always-on access to the device. In many situations, however, cellular is the only feasible choice. Additional security measures such as client-initiated VPN (Virtual Private Networks) are often used with cellular internet connections to ensure the integrity of the device.
Pots remains popular because of its low cost and security. Pots can be used for both direct dial connections and internet connections. Pots is a good choice for applications that do not require heavy data transfer as it continues to be a slower method of delivery. DSL (Digital Subscriber Line) running over pots is quite a bit faster and can be configured for an always-on, firewall-secured connection at a relatively low price.
Other network possibilities include satellite internet service, GPS technologies, dedicated long-range RF, infrared and more. These are seldom used due to a combination of factors including price, distance or stability.
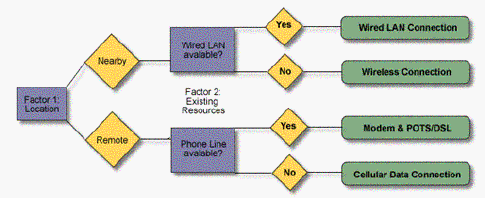
It may seem confusing when choosing a network type but it is usually quite simple. The network of choice is, in most cases, dictated by two factors: location and existing resources including the availability of phone or data lines. The figure above shows the decision process based on these factors.
M2M components
There are basically four components in an M2M system: 1) the intelligent device (machine or appliance) where the data originates, 2) the gateway that extracts and translates data, 3) the network which serves the data and 4) the remote client which ultimately receives the data. M2M software applications are optional but can facilitate communications, enable web access and provide the user interface.
Please see the following pages to continue with this preventive maintenance technology article...
The intelligent device: where the data originates
The gateway: translates and passes the data to the network
The network: the connectivity that serves data to the remote client
The remote client: the destination of the information
| Marty Huff - MSI Tec, Inc. About the author: Marty Huff is an it professional with MSI Tec and can be reached directly at 720-875-9835 or by email at mailto:martyh@msitec.com. MSI Tec is a provider of intelligent machine control components and systems, and the value adding engineering resources for the successful identification and implementation of their use.
Marty is esponsible for M2M systems design, programming and installation and is available for dedicated training programs and seminars on the subject of M2M. Don Fitchett, business industrial network, contributor to this article. |
See also

 Nokia and sierra wireless are two major players in the forefront of wireless and cellular hardware.
Nokia and sierra wireless are two major players in the forefront of wireless and cellular hardware.